Hey guys.
So I’ve been a supporter of Proton Mail since the first waiting list was established. Since then, they have grown and developed many new products. They were always solid on privacy until a few years ago when the gave up a user’s recovery email address. A lot of proton followers were outraged. One of Proton’s responses for that situation “If we were Google, we would have given up more than just an email address.” Really? Comparing yourself to Satan is good how? (1st red flag?)
After that incident, Proton changed their terms of service and removed their no logging policy. (2nd red flag)
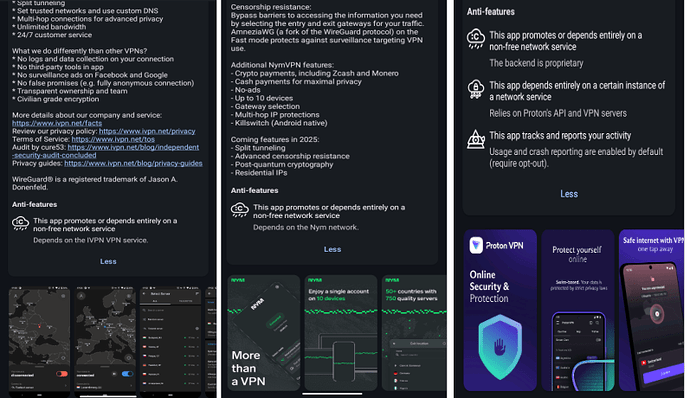
Now, I was comparing VPNs on F-Droid, IVPN, Nym and ProtonVPN. I noticed the Anti-features listed on ProtonVPN, Tracks and reports your activity? WTF? Ok, you can turn if off, if you remember and you know better, but a lot of peeps don’t or won’t. (3rd red flag?)
Maybe Proton is getting to too big and starting to think like google, maybe not. I just thought this would be an interesting topic to post since a lot of our community members uses ProtonVPN.
Very interesting @romluk - I had not seen that! I too have been a big protonmail user for several years and gradually used more of their services as they have come on line. But hadn’t seen the detail of this.
EDIT: But I agree with @jantinzi and @xancudo in their posts below, which sums it up pretty well.
I have read the article above 3 times. what is clear in this instance is that the person who had their EMAIL account and subsequent IP address logged happened due to a court order. Further, It seems as though the person was not using any vpn nor did they encrypt their email. The article gives a solution…Use a good vpn, use a secure browser along with all the ad/tracking blocked and use a system ad/tracker and no logging could have been done that would have revealed anything. Brax3 avails all the above to the user. Choose and install the vpn of your choice, encrypt what ever email client you use. Enable all the security measures available in the IODE browser or browser of your choice. Lock down all your apps with the included system security tool “trebuchet” and you should not have to worry,Short answer…if you are worried about proton logging your email/Ip, dont give them anything to log that will be of use to any nefarious actors. That is my understanding from the article…I could be wrong.
So this has been hashed 100 times… What I read was that the agency found out, or guessed the address.
However… on that point…
and while I’m not saying the article is right or wrong, or you are correct or incorrect, but as stated by @jantinzi , one needs to comb through all the features, and tighten to the point of feeling safe. That is the end-user’s responsibility. Not Proton’s. Personally, for my need, Proton is just fine.
The article I read when like this… A couple of years ago, Proton was served, to provide access to an email account that some agency who wanted access to. Proton has to comply, by law, even even in their own country. So they provided that access (and probably data), in it’s full encrypted state, and without the user’s knowledge, which was also part of the order.
Well, that agency was able to get into that data, because of some of the settings the user had setup on the account, specifically with Recovery.
If you go into your Proton account, you will find a section related to YOUR RECOVERY OPTIONS. In those options, there are places where you can place recovery emails, and recovery phone numbers. By using those options, or by guessing those options, and getting court ordered access to those items as well (without the user’s knowledge) , the agency was able to access the data via those recovery options. This was a failure on the user’s part, not Proton. They have to give what they know, or what their users put into the account.
This is what their page says, and I have to believe it’s true.
Personally, I remove ALL recovery options with the exception of codes. That’s my one recovery method. No phone, no email address.
Yup…that is exactly how I read it.
This brings up an important point to remember regarding technology companies and your connection to their services. If you have a device, but are not a paying customer or subscriber, law enforcement with a court order can compel these companies to activate services, not tell the user, and then log the activities.
One example of this is with GM vehicles and OnStar. If you have an OnStar equipped vehicle, but do not pay for the subscription, law enforcement can compel GM with a court order to turn on OnStar services. This, combined with a non-disclosure order, will allow the authorities to capture any and all data that OnStar can collect. All of this happens without your knowledge and without you ever consenting to the user agreements and privacy policies of the service.
A second example, also involving vehicles, is cellular service. If you have an infotainment system that has mobile data capabilities, that vehicle will connect to the cellular networks regardless of whether you are paying for the data services or not. Law enforcement, armed with your VIN, can compel the auto manufacturer to disclose the IMEI/IMSI of your infotainment system and can then obtain court orders or search warrants for the cellular data records, namely location data.
The main point, in the United States anyways, is that if you own a device that is capable of data collection, regardless of whether you are a paying and consenting customer, then law enforcement can compel the service provider to log and collect data. This is true of VPNs, auto manufacturers, cloud based camera systems, ect.
It is a brave new world we are living in. ![]()
Exactly. That guy’s sloppy OPSEC was more to blame than Proton who was compelled by a court order. I actually find it refreshing that they updated their website after being “caught,” which was a disingenuous way of describing what had transpired.
My general question is why do you assume that you can hide while using the internet. You can take all the normal precautions for privacy but from there on if they are looking for you they will find you. Why do you assume for example that Proton and any other VPN service isn’t a 3-lettter agency asset? Why do you assume that they don’t keep logs, that the government can’t force them to hand out the logs and that the government can’t survey specific points of the network to know who and how is using the VPN. If you’re doing something illegal it’s not wise to advertise here what devices and VPNs you’re using. If you are a government agent then you are playing smart posting in here.
I agree with @george completely. If you are hiding from the government, using the internet or cellular devices is a great way to get caught. The BraX3 phone is for privacy from Big Tech and the surveillance economy, not for evading MI-6.
Recovery options can be one more back door.
Do the best, assume the worst.
Are we ZOOGLED Are we ZOOGED OR could we also be GATEZindowed? AMAzoned by the AWS Monster?
No matter how we are, we are still Zucked over until we all get Candy Crushed. https://www.youtube.com/watch?v=-YPnLI0rvyU&list=PLL-sMa2lHYj3WIjaelOPbnIJVKmp9b4yc